Case Studies
Explore detailed case studies showcasing how our solutions have transformed businesses, driving efficiency, growth, and innovation across various industries.
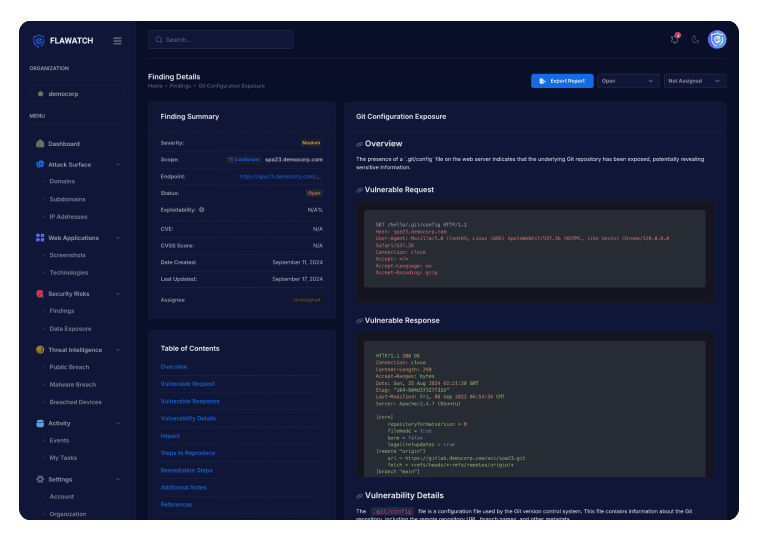
Security Misconfigurations Detection

Addressing Vulnerabilities Through Collaborative Automation
Automating security misconfiguration detection helps teams identify and fix vulnerabilities across systems.
Security Misconfigurations Detection

Addressing Vulnerabilities Through Collaborative Automation
Automating security misconfiguration detection helps teams identify and fix vulnerabilities across systems.
Security Misconfigurations Detection

Addressing Vulnerabilities Through Collaborative Automation
Automating security misconfiguration detection helps teams identify and fix vulnerabilities across systems.
Security Misconfigurations Detection

Addressing Vulnerabilities Through Collaborative Automation
Automating security misconfiguration detection helps teams identify and fix vulnerabilities across systems.
Risk Exposure Reduction

Strategic Solutions for Continuous Risk Mitigation
Discover how contextualized risk management reduces your attack surface while enhancing efficiency and organizational security.
Risk Exposure Reduction

Strategic Solutions for Continuous Risk Mitigation
Discover how contextualized risk management reduces your attack surface while enhancing efficiency and organizational security.
Risk Exposure Reduction

Strategic Solutions for Continuous Risk Mitigation
Discover how contextualized risk management reduces your attack surface while enhancing efficiency and organizational security.
Risk Exposure Reduction

Strategic Solutions for Continuous Risk Mitigation
Discover how contextualized risk management reduces your attack surface while enhancing efficiency and organizational security.
Vulnerability Assessment

From Intrusion Likelihood to Business Impact—A Smarter Approach to Vulnerability Management
Flawatch’s vulnerability assessment shifts focus from endless patching to prioritizing critical risks and remediation.
Vulnerability Assessment

From Intrusion Likelihood to Business Impact—A Smarter Approach to Vulnerability Management
Flawatch’s vulnerability assessment shifts focus from endless patching to prioritizing critical risks and remediation.
Vulnerability Assessment

From Intrusion Likelihood to Business Impact—A Smarter Approach to Vulnerability Management
Flawatch’s vulnerability assessment shifts focus from endless patching to prioritizing critical risks and remediation.
Vulnerability Assessment

From Intrusion Likelihood to Business Impact—A Smarter Approach to Vulnerability Management
Flawatch’s vulnerability assessment shifts focus from endless patching to prioritizing critical risks and remediation.
Active Directory Security

How Continuous Monitoring and Prioritized Remediation Keep Active Directory Safe
Protect your network’s core by safeguarding Active Directory through real-time risk analysis and focused remediation.
Active Directory Security

How Continuous Monitoring and Prioritized Remediation Keep Active Directory Safe
Protect your network’s core by safeguarding Active Directory through real-time risk analysis and focused remediation.
Active Directory Security

How Continuous Monitoring and Prioritized Remediation Keep Active Directory Safe
Protect your network’s core by safeguarding Active Directory through real-time risk analysis and focused remediation.
Active Directory Security

How Continuous Monitoring and Prioritized Remediation Keep Active Directory Safe
Protect your network’s core by safeguarding Active Directory through real-time risk analysis and focused remediation.
Cloud Security

Simplifying Cloud Exposure Management
We delivers visibility and efficiency, enabling cloud teams to prioritize and remediate critical threats in multi-cloud environments.
Cloud Security

Simplifying Cloud Exposure Management
We delivers visibility and efficiency, enabling cloud teams to prioritize and remediate critical threats in multi-cloud environments.
Cloud Security

Simplifying Cloud Exposure Management
We delivers visibility and efficiency, enabling cloud teams to prioritize and remediate critical threats in multi-cloud environments.
Cloud Security

Simplifying Cloud Exposure Management
We delivers visibility and efficiency, enabling cloud teams to prioritize and remediate critical threats in multi-cloud environments.
Let us Hunt Your Security Flaws
Discover how Flawatch protects your digital assets and minimizes risks to your attack surface.

Let us Hunt Your Security Flaws
Discover how Flawatch protects your digital assets and minimizes risks to your attack surface.


Let us Hunt Your Security Flaws
Discover how Flawatch protects your digital assets and minimizes risks to your attack surface.


Let us Hunt Your Security Flaws
Discover how Flawatch protects your digital assets and minimizes risks to your attack surface.



Continuously watching out for security flaws

Continuously watching out for security flaws

Continuously watching out for security flaws

Continuously watching out for security flaws


