See Flawatch in Action
Experience how Flawatch can help you manage and secure your external exposure and attack surface.
Let us Hunt Your Security Flaws
Discover how Flawatch protects your digital assets and minimizes risks to your attack surface.

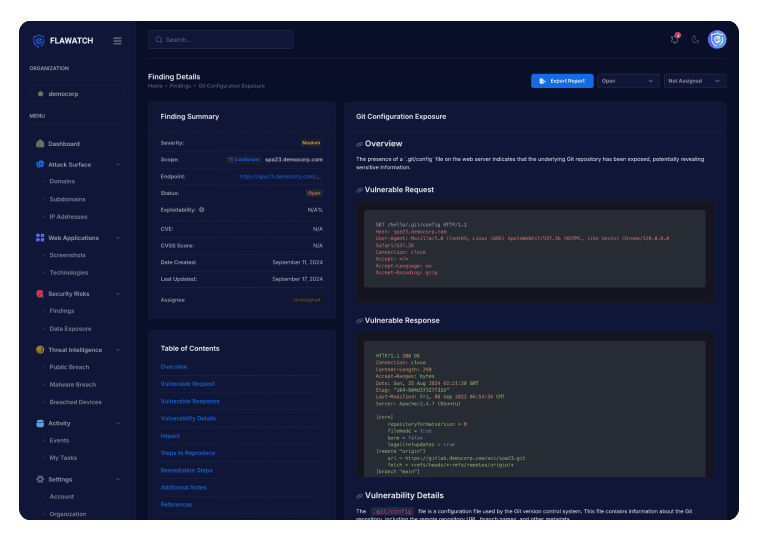
Let us Hunt Your Security Flaws
Discover how Flawatch protects your digital assets and minimizes risks to your attack surface.


Let us Hunt Your Security Flaws
Discover how Flawatch protects your digital assets and minimizes risks to your attack surface.


Let us Hunt Your Security Flaws
Discover how Flawatch protects your digital assets and minimizes risks to your attack surface.


Common Questions
Haven’t found what you’re looking for? Contact us
What is Cyber Threat Intelligence-backed Attack Surface Management (CTI-ASM)?

CTI-ASM combines threat intelligence with attack surface management to deliver real-time insights into vulnerabilities and monitor threats from dark web forums, Telegram channels, and more.
How Does Flawatch Monitor the Dark Web and Illicit Channels?

What types of threats can our CTEM solution help mitigate?

What Benefits Does Attack Surface Monitoring Offer to CISOs and Security Teams?

How Does Our Solution Manage Risks from Third-Party Integrations and Shadow IT?

What is Cyber Threat Intelligence-backed Attack Surface Management (CTI-ASM)?

CTI-ASM combines threat intelligence with attack surface management to deliver real-time insights into vulnerabilities and monitor threats from dark web forums, Telegram channels, and more.
How Does Flawatch Monitor the Dark Web and Illicit Channels?

What types of threats can our CTEM solution help mitigate?

What Benefits Does Attack Surface Monitoring Offer to CISOs and Security Teams?

How Does Our Solution Manage Risks from Third-Party Integrations and Shadow IT?

What is Cyber Threat Intelligence-backed Attack Surface Management (CTI-ASM)?

CTI-ASM combines threat intelligence with attack surface management to deliver real-time insights into vulnerabilities and monitor threats from dark web forums, Telegram channels, and more.
How Does Flawatch Monitor the Dark Web and Illicit Channels?

What types of threats can our CTEM solution help mitigate?

What Benefits Does Attack Surface Monitoring Offer to CISOs and Security Teams?

How Does Our Solution Manage Risks from Third-Party Integrations and Shadow IT?

What is Cyber Threat Intelligence-backed Attack Surface Management (CTI-ASM)?

CTI-ASM combines threat intelligence with attack surface management to deliver real-time insights into vulnerabilities and monitor threats from dark web forums, Telegram channels, and more.
How Does Flawatch Monitor the Dark Web and Illicit Channels?

What types of threats can our CTEM solution help mitigate?

What Benefits Does Attack Surface Monitoring Offer to CISOs and Security Teams?

How Does Our Solution Manage Risks from Third-Party Integrations and Shadow IT?


Continuously watching out for security flaws

Continuously watching out for security flaws

Continuously watching out for security flaws

Continuously watching out for security flaws


