Threat Exposure Management
Covering Every
Hacker's Strategy
AI-Powered Automated Offensive Security
Backed by Real-Time Threat Intelligence Insights.

Companies we helped worldwide
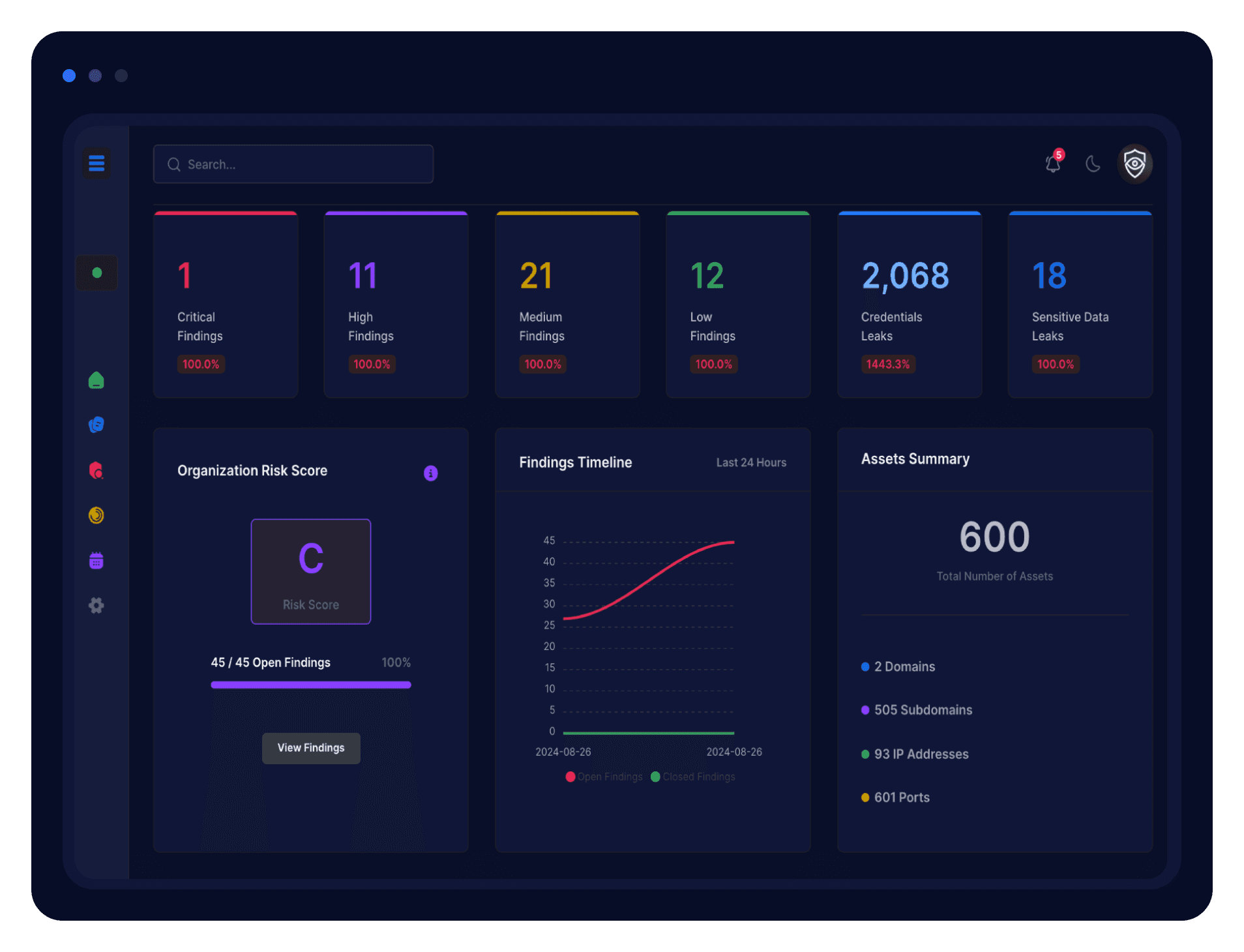
Threat Exposure Detection
Continuous Threat Exposure Management (CTEM) to identify and address risks in real time.
Attack Surface Mapping
External Attack Surface Management (EASM) for full visibility of your digital footprint.
ASM Powered by Threat Intelligence
Flawtrack’s ASM and Threat Intelligence platform provides continuous monitoring and actionable insights into your attack surface.
Monitor the Dark Web
and Illicit Communities
Stay ahead of cybercriminals with real-time monitoring of dark web forums, markets, Telegram channels, and other hidden spaces.
Understand your
External Attack Surface
Gain full visibility of your digital perimeter with Flawtrack ASM’s asset discovery and monitoring.
Year 2024
Cost of a data breach
Year 2025
$10.5B
The global cybercrime costs
Year 2023
43%
cyberattacks against SMEs
Q1 2023 Only
15M
Data Breaches Exposed
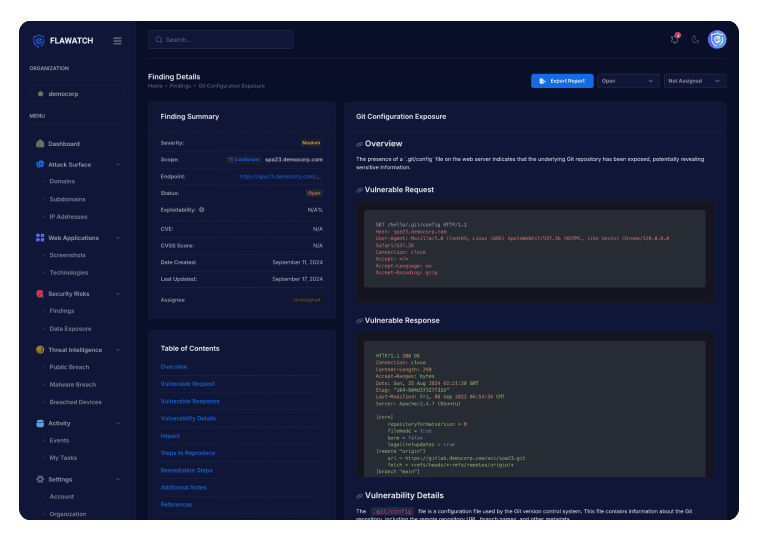
The Automated Hacker
Flawatch identifies exposure changes in real time and evaluates risks from a hacker’s perspective using AI.

116k+

3.4%
New Assets Found Daily
Mapping
the unknown
With passive data sources, active scanning, and machine learning, Flawtrack uncovers digital assets and complex attack paths often overlooked by security teams.
Thinking Like
a Hacker
Flawatch identifies how misconfigurations, exposed credentials, permissions, and vulnerabilities shape your security risks.

Cutting through
the noise
Flawtrack combines context with a broader exposure analysis, enabling teams to prioritize risks attackers are most likely to exploit.
Protecting Millions Worldwide
We’ve helped organizations secure the personal information of millions of their customers, preventing leaks and breaches.
Common Questions
Haven’t found what you’re looking for? Contact us